There are two different modes of ZTNA in FortiOS. One is IP/MAC based filtering and the other one full ZTNA via a “access-proxy”. To create a full ZTNA configuration with FortiOS 7.x the following steps are required:
EMS/FortiClient Configuration
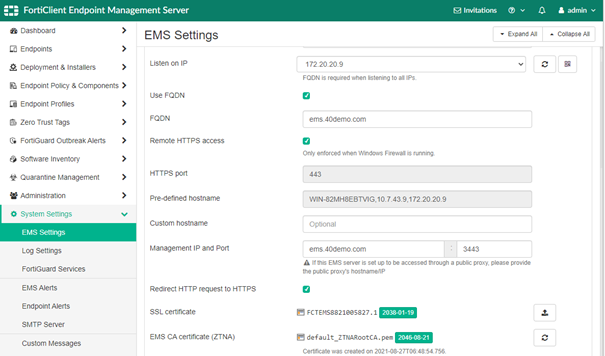
Configure the wanted certificate and define the external FQDN from which the EMS Server is reachable:
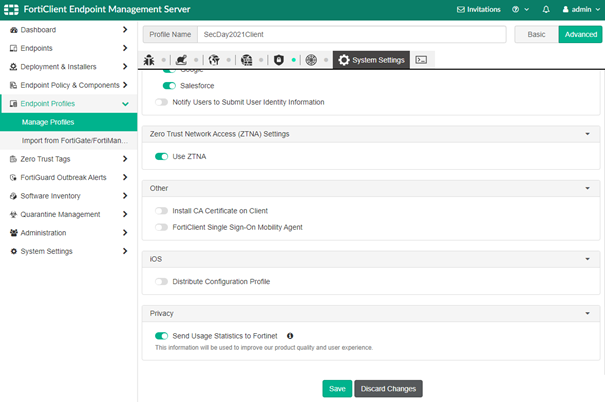
Enable ZTNA on the Endpoint Profile:
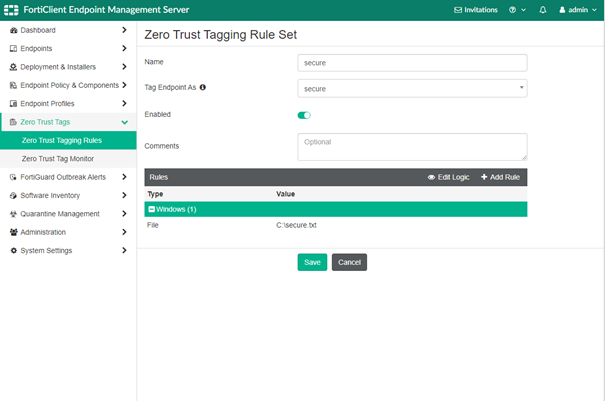
Define the ZTNA tagging rules. Very complex rules can be created. To showcase this, just basic text file checks are being used:
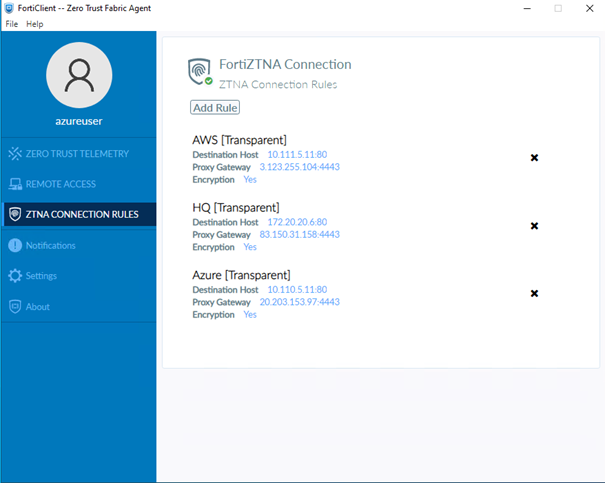
Create ZTNA connection rules on FortiClient:
FortiGate configuration
Configure the firewall access-proxy:
ASSDWANDEMO-FGT-A # config firewall access-proxy
ASSDWANDEMO-FGT-A (access-proxy) # edit "Webserver"
config firewall access-proxy
edit "Webserver"
set vip "Webserver"
set client-cert enable
config api-gateway
edit 1
set service http
config realservers
edit 1
set ip 10.110.5.11
set port 80
next
end
next
end
next
end
Configure the ZTNA rule on FGT:
ASSDWANDEMO-FGT-A # config firewall proxy-policy
ASSDWANDEMO-FGT-A (proxy-policy) # edit "1"
config firewall proxy-policy
edit 1
set uuid e646e97a-1593-51ec-9a8d-30f8307a8a47
set name "Web-Access"
set proxy access-proxy
set access-proxy "Webserver"
set srcintf "port1"
set srcaddr "all"
set dstaddr "all"
set ztna-ems-tag "FCTEMS8821005827_secure"
set action accept
set schedule "always"
set logtraffic all
next
end
Check if the ZTNA tags are being synchronized: